IoT Hack
Dec. 26th, 2025 12:02 pmSomeone hacked an Italian ferry.
It looks like the malware was installed by someone on the ferry, and not remotely.
Someone hacked an Italian ferry.
It looks like the malware was installed by someone on the ferry, and not remotely.

It’s no surprise that NVIDIA is gradually dropping support for older videocards, with the Pascal (GTX 10xx) GPUs most recently getting axed. What’s more surprising is the terrible way that this is being handled by certain Linux distributions, with Arch Linux currently a prime example.
On these systems, updating the OS with a Pascal, Maxwell or similarly unsupported GPU will result in the new driver failing to load and thus the user getting kicked back to the CLI to try and sort things back out there. This issue is summarized by [Brodie Robertson] in a recent video.
Here the ‘solution’ is to switch to a legacy option that comes from the Arch User Repository (AUR), which feels somewhat sketchy. Worse is that using this legacy option breaks Steam as it relies on official NVIDIA dependencies, which requires an additional series of hacks to hopefully restore this functionality. Fortunately the Arch Wiki provides a starting point on what to do.
It’s also worth noting that this legacy driver on the AUR is being maintained by [ventureo] of the CachyOS project, whose efforts are the sole reason why these older NVIDIA cards are still supported at all on Linux with the official drivers. While there’s also the Nouveau driver, this is effectively a reverse-engineering project with all of the problems that come with such an effort, even if it may be ‘good enough’ for older GPUs.
Blacksadin kumppani Weekly astuu valokeilaan! Uusi Blacksadin maailmaan sijoittuva upea albumi ilmestyy 29.12.2025.

Lehtimieslumikko Weekly on auttanut (tai ainakin yrittänyt auttaa) Blacksadia lähes kaikissa kissaetsivän tärkeimmissä tapauksissa. Albumissa Valkoinen valtakunta ensiesiintymisensä tehnyt punaturkkinen What’s Newsin tutkija ja valokuvaaja on osoittautunut sitkeäksi ja oikeamieliseksi apumieheksi – niin ärsyttävä kun hän osaa väliin ollakin. Mutta mistä Weekly oikein on peräisin, millainen on hänen tarinansa?

Uunituore Blacksad esittää – Weekly paljastaa, miten lumikkoveijari vietti nuoruutensa – ja miten hänestä kovien koettelemusten kautta kehkeytyi sinnikäs uutishaukka. Ilmenee, että Weeklyn suku on paennut Venäjältä Amerikkaan, ja nuori Weekly elelee New Yorkissa ärhäkän isoäitinsä kanssa. Isoäiti uneksii kasakoista samalla kun hänen holhokkinsa etsii omaa paikkaansa synkeässä suurkaupungissa. Ja levoton lumikko ehtii kokeilla monenlaisia ammatteja, ennen kuin hän löytää todellisen kutsumuksensa.

Mutta toki sodanjälkeinen, kasvukautta elävä suurkaupunki tarjoaakin uutteralle nuorukaiselle monia tilaisuuksia. Poliisin kuvaajana aloitteleva Weekly päätyy mummon ansiosta apulaiseksi hautaustoimistoon, jonka harmaan julkisivun takana vaikuttaisi tapahtuvan jotakin outoa. Hauturin rouva, pastori Lubansky, johtaa äänekästä kansalaisliikettä, joka pyrkii kieltämään nuorisoa turmelevat sarjakuvalehdet! Weeklyllä sen sijaan on ideoita kauhusarjakuvien piristämiseksi… mutta mahtavatko rikosfantasiat muuttua karuksi todeksi?

Blacksad esittää – Weekly on mainio ja oleellinen lisäys Blacksadin kiehtovaan maailmaan. Albumin on käsikirjoittanut Juan Díaz Canales, joka on laatinut tarinat kaikkiin aiempiinkin Blacksad-seikkailuihin. Kuvittajana loistaa italialainen Giovanni Rigano, jonka taitava piirrosjälki on tätä ennen koristanut mm. Artemis Fowlin sekä Ihmeperheen sarjakuvaversioita. Yhdessä Canales ja Rigano ovat luoneet eloisan, tunnelmallisen ja jännittävän vision lähes sadan vuoden takaisesta New Yorkista – ja onnistuneet siinä samalla käsittelemään myös sarjakuvan historiaa fiktion keinoin.

Blacksad esittää – Weekly on kovakantinen, 64-sivuinen suurikokoinen värialbumi, ja se ilmestyy 29.12.2025. Weeklyn voit ostaa kaikista hyvin varustetuista kirja- ja sarjakuvakaupoista sekä Story House Egmontin verkkokaupasta. Ja muistathan, että kaikki aiemmat Blacksad-sarjan albumit ovat nyt saatavina pehmytkantisina versioina!

The post Blacksad esittää – Weekly appeared first on Story House Egmont.

Names and labels are difficult. Take this “3D Printed” water-cooling loop by [Visual Thinker] on YouTube. It undeniably uses 3D printing — but it also uses silicone casting and laser-cut acrylic, too. All of these are essential parts, yet only 3D printing gets top billing in his thumbnail. At least the version we saw, anyway; the A/B testing game YouTubers play means that may change.
Perhaps that’s simply due to the contrast with [Visual Thinker]’s last build, where the “distro plate” that acts to plumb most of the coolant was made of layers of CNC-routed acrylic, held water-tight with O-rings. Not wanting to wait for his next build to be fabricated, and not wanting to take up CNC machining himself, [Visual Thinker] fell back on tools many of us have and know: the 3D printer and laser cutter.
In this project, the end plates of the cooling loop are still clear acrylic, but he’s using a laser cutter to shape them. That means he cannot route out gaps for o-rings like in the last project, so that part gets 3D printed. Sort of. Not trusting the seal a 3D printed gasket would be able to give him, [Visual Thinker] opts to use his 3D printer to create a mold to cast a seal in silicone. Or perhaps “injection-mold” would be a better word than cast; he’s using a large syringe to force the degassed silicone into the mold. The end part is three pieces: a 3D printed spacer holding two acrylic plates, with the cast-silicone gasket keeping the whole thing water-tight to at least 50 psi, 10x the operating pressure of his PC.
After that success, he tries replacing the printed spacer with acrylic for a more transparent look. In that version only temporary shims that are used to form the mold are 3D printed at all, and the rest is acrylic. Even if you’re not building a water-cooled art PC, it’s still a great technique to keep in your back pocket for fluid channeling.
In some ways, this technique is the exact opposite of the copper-pipe steampunk builds we’ve featured previously. Those were all about pretty plumbing, while with a distro plate you hardly need pipes at all. Like any water-cooled project, it’ll need a radiator, which could be a hack in and of itself.
Thanks to [Joey Marino] for this hot tip about PC cooling.
A little over two years ago, I wrote an article titled SSH agent forwarding and tmux done right. In it, I described how SSH agent forwarding works—a feature that lets a remote machine use the credentials stored in your local ssh-agent instance—and how using a console multiplexer like tmux or screen often breaks it.
In that article, I presented the ssh-agent-switcher: a program I put together in a few hours to fix this problem. In short, ssh-agent-switcher exposes an agent socket at a stable location (/tmp/ssh-agent.${USER?} by default) and proxies all incoming credential requests to the transient socket that the sshd server creates on a connection basis.
In this article, I want to formalize this project by presenting its first actual release, 1.0.0, and explain what has changed to warrant this release number. I put effort into creating this formal release because ssh-agent-switcher has organically gained more interest than I imagined as it is solving a real problem that various people have.
When I first wrote ssh-agent-switcher, I did so to fix a problem I was having at work: we were moving from local developer workstations to remote VMs, we required SSH to work on the remote VMs for GitHub access, and I kept hitting problems with the ssh-agent forwarding feature breaking because I’m an avid user of tmux.
To explain the problem to my peers, I wrote the aforementioned article and prototyped ssh-agent-switcher after-hours to demonstrate a solution. At the end of the day, the team took a different route for our remote machines but I kept using this little program on my personal machines.
Because of work constraints, I had originally written ssh-agent-switcher in Go and I had used Bazel as its build system. I also used my own shtk library to quickly write a bunch of integration tests and, because of the Bazel requirement, I even wrote my first ruleset, rules_shtk, to make it possible.
The program worked, but due to the apparent lack of interest, I considered it “done” and what you found in GitHub was a code dump of a little project I wrote in a couple of free evenings.
Recently, however, ssh-agent-switcher stopped working on a Debian testing machine I run and I had to fix it. Luckily, someone had sent a bug report describing what the problem was: OpenSSH 10.1 had changed the location where sshd creates the forwarding sockets and even changed their naming scheme, so ssh-agent-switcher had to adapt.
Fixing this issue was straightforward, but doing so made me have to “touch” the ssh-agent-switcher codebase again and I got some interest to tweak it further.
As I wanted to modernize this program, one thing kept rubbing me the wrong way: I had originally forced myself to use Go because of potential work constraints. As these requirements never became relevant and I “needed to write some code” to quench some stress, I decided to rewrite the program in Rust. Why, you ask? Just because I wanted to. It’s my code and I wanted to have fun with it, so I did the rewrite.
Which took me into a detour. You see: while command line parsing in Rust CLI apps is a solved problem, I had been using the ancient getopts crate in other projects of mine out of inertia. Using either library requires replicating some boilerplate across apps that I don’t like, so… I ended up cleaning up that “common code” as well and putting it into a new crate aptly-but-oddly-named getoptsargs. Take a look and see if you find it interesting… I might write a separate article on it.
Doing this rewrite also made me question the decision to use Bazel (again imposed by constraints that never materialized) for this simple tool: as much as I like the concepts behind this build system and think it’s the right choice for large codebases, it was just too heavy for a trivial program like ssh-agent-switcher. So… I just dropped Bazel and wrote a Makefile—which you’d think isn’t necessary for a pure Rust project but remember that this codebase includes shell tests too.
With the Rust rewrite done, I was now on a path to making ssh-agent-switcher a “real project” so the first thing I wanted to fix were the ugly setup instructions from the original code dump.
Here is what the project README used to tell you to write into your shell startup scripts:
if [ ! -e "/tmp/ssh-agent.${USER}" ]; then
if [ -n "${ZSH_VERSION}" ]; then
eval ~/.local/bin/ssh-agent-switcher 2>/dev/null "&!"
else
~/.local/bin/ssh-agent-switcher 2>/dev/null &
disown 2>/dev/null || true
fi
fi
export SSH_AUTH_SOCK="/tmp/ssh-agent.${USER}"Yikes. You needed shell-specific logic to detach the program from the controlling session so that it didn’t stop running when you logged out, as that would have made ssh-agent-switcher suffer from the exact same problems as regular sshd socket handling.
The solution to this was to make ssh-agent-switcher become a daemon on its own with proper logging and “singleton” checking via PID file locking. So now you can reliably start it like this from any shell:
~/.local/bin/ssh-agent-switcher --daemon 2>/dev/null || true
export SSH_AUTH_SOCK="/tmp/ssh-agent.${USER}"I suppose you could make systemd start and manage ssh-agent-switcher automatically with a per-user socket trigger without needing the daemonization support in the binary per se… but I do care about more than just Linux and so assuming the presence of systemd is not an option.
With that done, I felt compelled to fix a zero-day TODO that kept causing trouble for people: a fixed-size buffer used to proxy requests between the SSH client and the forwarded agent. This limitation caused connections to stall if the response from the ssh-agent contained more keys than fit in the buffer.
The workaround had been to make the fixed-size buffer “big enough”, but that was still insufficient for some outlier cases and came with the assumption that the messages sent over the socket would fit in the OS internal buffers in one go as well. No bueno.
Fixing this properly required one of the following:
adding threads to handle reads and writes over two sockets in any order,
dealing with the annoying select/poll family of system calls, or
using an async runtime and library (tokio) to deal with the event-like nature of proxying data between two network connections.
People dislike async Rust for some good reasons, but async is the way to get to the real fearless concurrency promise. I did not fancy managing threads by hand, and I did not want to deal with manual event handling… so async it was.
And you know what? Switching to async had two immediate benefits:
Handling termination signals with proper cleanup became straightforward. The previous code had to install a signal handler and deal with potential races in the face of blocking system calls by doing manual polling of incoming requests, which isn’t good if you like power efficiency. Using tokio made this trivial and in a way that I more easily trust is correct.
I could easily implement the connection proxying by using an event-driven loop and not having to reason about threads and their terminating conditions. Funnily enough, after a couple of hours of hacking, I felt proud of the proxying algorithm and the comprehensive unit tests I had written so I asked Gemini for feedback, and… while it told me my code was correct, it also said I could replace it all with a single call to a tokio::io primitive! Fun times. I still don’t trust AI to write much code for me, but I do like it a lot to perform code reviews.
Even with tokio in the picture and all of the recent new features and fixes, the Rust binary of ssh-agent-switcher is still smaller (by 100KB or so) than the equivalent Go one and I trust its implementation more.
Knowing that various people had found this project useful over the last two years, I decided to conclude this sprint by creating an actual “formal release” of ssh-agent-switcher.
Formal releases require:
Documentation, which made me write a manual page.
A proper installation process, which made me write a traditional make install-like script because cargo install doesn’t support installing supporting documents.
A tag and release number, which many people forget about doing these days but are critical if you want the code to be packaged in upstream OSes.
And with that, ssh-agent-switcher 1.0.0 went live on Christmas day of 2025. pkgsrc already has a package for it; what is your OS waiting for? 😉
Revolution Team, the modding team behind GTA Vice City NextGen Edition, has announced GTA: San Andreas NextGen Edition. This project aims to bring the entirety of Grand Theft Auto: San Andreas to GTA 5’s RAGE Engine. Like GTA Vice City NextGen Edition, GTA San Andreas NextGen Edition will feel like a remaster of the original … Continue reading Modders are bringing GTA: San Andreas to GTA 5’s RAGE Engine
The post Modders are bringing GTA: San Andreas to GTA 5’s RAGE Engine appeared first on DSOGaming.
Modder ‘Kongmeng’ has released an amazing new mod for Dragon Ball FighterZ. This mod allows you to play as Yami Yugi from the Yu-Gi-Oh!! anime. Normally, you’d assume that this would have been a simple character swap mod. But no, this is more than that. Yugi has his own moves, and he can summon a … Continue reading Dragon Ball FighterZ Just Got an Amazing Yu-Gi-Oh!! Character Mod
The post Dragon Ball FighterZ Just Got an Amazing Yu-Gi-Oh!! Character Mod appeared first on DSOGaming.
Forever Entertainment has announced that FRONT MISSION 3: Remake will be coming to PC on January 30th, 2026. To celebrate this announcement, the publisher released a free PC demo that you can download from Steam. FRONT MISSION 3: Remake is a tactical RPG set in a future where nations and corporations compete for dominance in … Continue reading FRONT MISSION 3: Remake is coming to PC on January 30th, PC demo released
The post FRONT MISSION 3: Remake is coming to PC on January 30th, PC demo released appeared first on DSOGaming.

Holiday cookies are a joy, and to make things a bit more fun, [The Skjegg] created the Cookie Launcher. At the touch of a button, a door opens and the tin launches a cookie (and perhaps a few crumbs) skyward. Catching it is up to the operator, but since the tin can hold up to 40 cookies at once (39 in a magazine and 1 in the launcher), there’s enough to get some practice in.
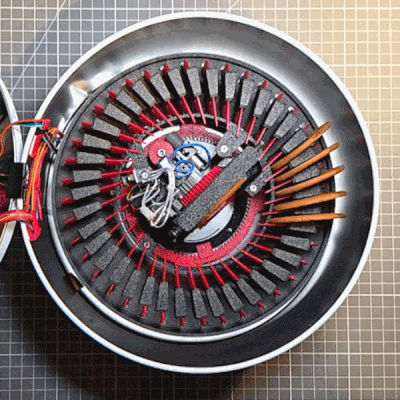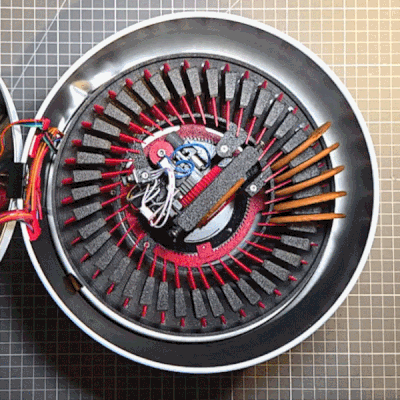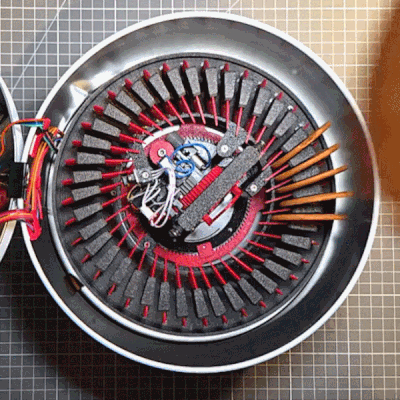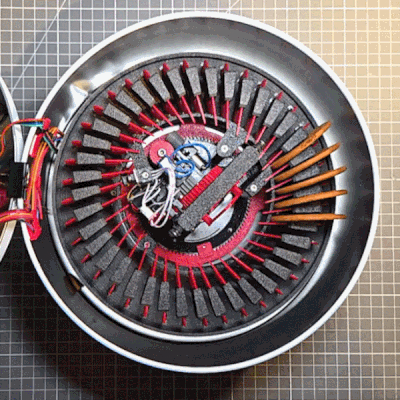 The design is a real thing of beauty, from the rotary cookie holder to the ejector. Individual cookies are held in a pan-style magazine that rotates until a tasty disk is lined up with the ejector. The red separators aren’t just for show, either. The little inward protrusion on each one interacts with an optical sensor to ensure the system always knows when things are lined up.
The design is a real thing of beauty, from the rotary cookie holder to the ejector. Individual cookies are held in a pan-style magazine that rotates until a tasty disk is lined up with the ejector. The red separators aren’t just for show, either. The little inward protrusion on each one interacts with an optical sensor to ensure the system always knows when things are lined up.
The launcher design is pretty neat, too. There’s a platform that uses two smooth bolts as guides, and elastic bands to store energy. A motor cranks it downward, where it locks into place. The rotary magazine then turns to line up a cookie, which gravity feeds into the launcher by rolling down an incline. When a cookie is in place, a door in the lid opens and the launcher platform releases, sending the cookie skyward.
The original concept for the Cookie Launcher involved voice activation, but training the voice module to trigger on custom Norwegian commands wasn’t very reliable. Luckily, a button is far more obedient. It may be a bit less magical to use, but in our opinion the physicality of a button push meshes perfectly well with the requirement to catch your own cookie.
You can get a good look at the operation and a detailed tour of the insides in the video, embedded below. Thanks to [Rohit] for sending in the tip!
If airborne cookies aren’t your bag, check out one a very different approach to hands-free cookie dispensing.

Perhaps the most beautiful aspect of mathematics is that it applies to literally everything, even things that do not exist in this Universe. In addition to this there are a number of alternative ways to represent reality, with Fourier space and its related transforms being one of the most well-known examples. An alternative to Euclidian vector space is called Hilbert space, as a real or complex inner product space, which is used in e.g. mathematical proofs. In relation to this, [Eli Bendersky] came up with the idea of treating programming language functions as vectors of a sort, so that linear algebra methods can be applied to them.
Of course, to get really nitpicky, by the time you take a function with its arguments and produce an output, it is no longer a vector, but a scalar of some description. Using real numbers as indices also somewhat defeats the whole point and claim of working in a vector space, never mind Hilbert space.
As with anything that touches upon mathematics there are sure to be many highly divisive views, so we’ll leave it at this and allow our esteemed readers to flex their intellectual muscles on this topic. Do you think that the claims made hold water? Does applying linear algebra to every day functions make sense in this manner, perhaps even hold some kind of benefit?

Facebook Marketplace provides you with a free grain silo, so what do you do with it? If you are [saveifforparts], you mix it with other materials and produce a retro-style rocket ship prop. Art project? Sure, we’ll call it that.
We have to admit, we also see rockets in everyday objects, and the silo does look the part. He also had some junk that looked like a nose cone, some tanks, and other assorted trash.
The electronics junk looks familiar, and after a thorough hose-down, he reused some of the front panels to drive a few sound effects. At least until some smoke came out of one of them. Adding a door proved the most challenging part.
The whole thing reminded us of a Captain Proton holodeck adventure. Honestly, if he had kept it horizontal, it would have made a fair Republic serial spaceship for Flash or Buck.
Useful? No. Cool. You bet. We doubt you’d replicate this, but we do hope it might inspire you to create your own whimsical project. Let us know when you do.
We hope he has a ray gun in there. He still has some blank bulkhead space. He may need a few more control panels.

 Although you can purchase many types of FDM filaments containing ‘carbon fiber’ these days, they are in no way related to the carbon fiber (CF) composite materials used for rocket hulls and light-weight bicycles. This is because the latter use continuous fibers, often in weaved CF mats, whereas the FDM filaments just use small, chopped, fragments of CF. Obviously this will not result in the same outcome, which makes it interesting that a company called Fibre Seek is now running a KickStarter for a very affordable co-extrusion FDM printer that can add continuous CF to any part. They also sent a few test parts to [Dr. Igor Gaspar] for testing against regular FDM CF prints.
Although you can purchase many types of FDM filaments containing ‘carbon fiber’ these days, they are in no way related to the carbon fiber (CF) composite materials used for rocket hulls and light-weight bicycles. This is because the latter use continuous fibers, often in weaved CF mats, whereas the FDM filaments just use small, chopped, fragments of CF. Obviously this will not result in the same outcome, which makes it interesting that a company called Fibre Seek is now running a KickStarter for a very affordable co-extrusion FDM printer that can add continuous CF to any part. They also sent a few test parts to [Dr. Igor Gaspar] for testing against regular FDM CF prints.
It should be noted here that continuous CF with FDM is not new, as Markforged already does something similar, though at a ‘Contact us for a price quote’ level. The advantage of the Fibre Seek solution is then the co-extrusion that would make printing with continuous CF much more flexible and affordable. Based on the (sponsored) [CNC Kitchen] video of a few weeks ago at a tradeshow, the FibreSeeker 3 printer is effectively a standard CoreXY FDM printer, with the special co-extrusion dual print head that allows for CF to be coated with the target thermoplastic before being printed as normal.
Unfortunately for [Igor] he did not have a FibreSeeker 3 to print on, and the print request for his usual test samples got mixed up by Fibre Seek, leaving him with only 4 out of 10 items to test with. This makes this a bit of an abbreviated test, but should still provide some useful data relative to the Polymaker PETG-CF filament that was used for comparison.
Based on the limited test set, it can be said that the FibreSeeker 3 parts did generally better than the PETG-CF parts, albeit with a few asterisks. Accordingly, [Igor] is left feeling somewhat confused by Fibre Seek, but sees the potential of this new co-extrusion technology. It just feels like the FibreSeeker 3 printer is not quite finished yet, and that the true value of this approach and this new printer will have to prove themselves.

Pagers were once a great way to get a message to someone out in public; they just had to be cool enough to have one. These days, they’re mostly the preserve of doctors and a few other niche operators. [Kyle Tryon] is bringing the beeper back, though, with a custom ESP32-based build.
The ESP32 is a great microcontroller for this kind of project, because it’s got WiFi and Bluetooth connectivity built right in. This let [Kyle] write some straightforward code so that it could receive alerts via MQTT. In particular, it’s set up to go off whenever there’s an app or service notification fired off by the Sentry platform. For [Kyle]’s line of work, it’s effectively an on-call beeper that calls them in when a system needs immediate attention. When it goes off, it plays the ringtone of your choice—with [Kyle] making it capable of playing tunes in Nokia’s old-school RTTTL music format.
The code was simple enough, and the assembly wasn’t much harder. By starting with an Adafruit ESP32 Reverse TFT Feather, the screen and buttons were all ready to go right out of the box. [Kyle] merely had to print up a rad translucent case on a resin printer to make it look like a sweet fashionable beeper from the 90s.
It’s a fun little project that should prove useful, while also being nicely reminiscent of a technology that has largely fallen by the wayside.
2025 is almost behind us. Contrary to last year’s article, our GOTY has gone live earlier. The reason we’ve decided to publish it earlier is so we can have enough time for the rest of our yearly articles. Because I know that a lot of you are waiting for our Top 10 Optimized PC Games … Continue reading Here are DSOGaming’s Games of the Year 2025
The post Here are DSOGaming’s Games of the Year 2025 appeared first on DSOGaming.